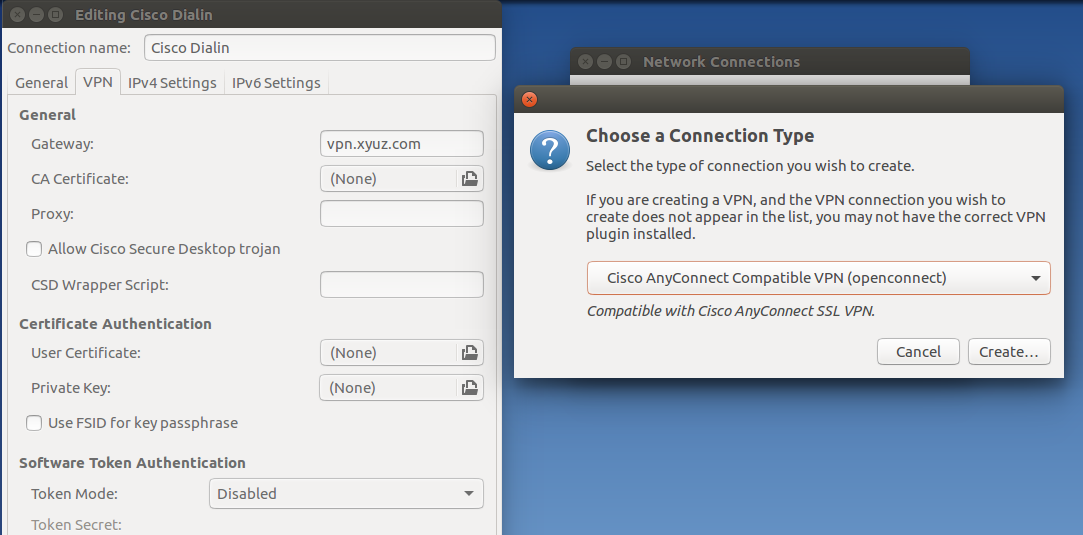
The AnyConnect NVM can be packaged with a pre-built AnyConnect Linux Kernel Module so that you do not need to build it on every target device, especially when the target devices have the same OS kernel version. Cisco AnyConnect is cross-platform. It can be used on Microsoft, Linux, and Mac operating systems. Depending on the plan used, it can connect thousands of laptops into a single encrypted connection. Powerful mobile defense. Cisco has developed a product that is useful for business with valuable assets distributed across the world. Cisco AnyConnectは、Windows 7、8、8.1、および10、Mac OS X 10.8以降、およびLinux Intel(x64)と互換性があります。 この記事の手順に従って、Ubuntu DesktopにCisco AnyConnect VPN Mobility Clientをインストールします。この記事では、Ubuntuバージョン20.04が使用されています。. An openconnect VPN server, which implements an improved version of the Cisco AnyConnect protocol, has also been written. OpenConnect is released under the GNU Lesser Public License, version 2.1. Development of OpenConnect was started after a trial of the Cisco AnyConnect client under Linux found it to have many deficiencies.
Here’s the simple steps for you to connect to a Cisco VPN in Ubuntu 18.04 LTS.
Cisco, an American company is the leading provider and manufacturer of enterprise network devices, telecommunication hardware, networking security and networking software.
According to computer profile as of April 2018, Cisco holds a 73.9% market which makes it the undisputed leader in its industry. Without further ado here
are the steps.
1. Install vpnc and network-manager-vpnc-gnome
2. Enter your password
3. Confirm installation
4. After successfully installing the required software it is time to configure it.
5. Add a new VPN connection
6. From the VPN type options, select Cisco Compatible VPN (vpnc)
7. Enter your VPN credentials and press Add
openconnect: Connect to Cisco AnyConnect VPN
Command to display openconnect manual in Linux: $ man 8 openconnect
NAME
openconnect - Connect to Cisco AnyConnect VPNSYNOPSIS
[Anyconnect Cisco Linux
--config configfile ][ -b,--background ][ --pid-file pidfile ][ -c,--certificate cert ][ -e,--cert-expire-warning days ][ -k,--sslkey key ][ -C,--cookie cookie ][ --cookie-on-stdin ][ --compression MODE ][ -d,--deflate ][ -D,--no-deflate ][ --force-dpd interval ][ -g,--usergroup group ][ -h,--help ][ --http-auth methods ][ -i,--interface ifname ][ -l,--syslog ][ --timestamp ][ -U,--setuid user ][ --csd-user user ][ -m,--mtu mtu ][ --basemtu mtu ][ -p,--key-password pass ][ -P,--proxy proxyurl ][ --proxy-auth methods ][ --no-proxy ][ --libproxy ][ --key-password-from-fsid ][ -q,--quiet ][ -Q,--queue-len len ][ -s,--script vpnc-script ][ -S,--script-tun ][ -u,--user name ][ -V,--version ][ -v,--verbose ][ -x,--xmlconfig config ][ --authgroup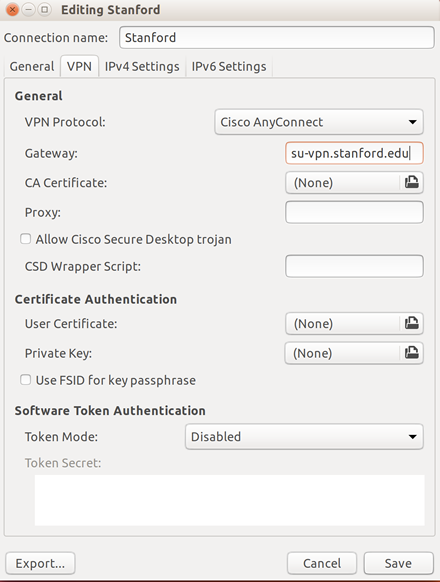 group ][ --authenticate ][ --cookieonly ][ --printcookie ][ --cafile file ][ --disable-ipv6 ][ --dtls-ciphers list ][ --dtls-local-port port ][ --dump-http-traffic ][ --no-cert-check ][ --no-system-trust ][ --pfs ][ --no-dtls ][ --no-http-keepalive ][ --no-passwd ][ --no-xmlpost ][ --non-inter ][ --passwd-on-stdin ][ --token-mode mode ][ --token-secret {secret[,counter]|@file} ][ --reconnect-timeout ][ --servercert sha1 ][ --useragent string ][ --os string ][https://]server[:port][/group]
group ][ --authenticate ][ --cookieonly ][ --printcookie ][ --cafile file ][ --disable-ipv6 ][ --dtls-ciphers list ][ --dtls-local-port port ][ --dump-http-traffic ][ --no-cert-check ][ --no-system-trust ][ --pfs ][ --no-dtls ][ --no-http-keepalive ][ --no-passwd ][ --no-xmlpost ][ --non-inter ][ --passwd-on-stdin ][ --token-mode mode ][ --token-secret {secret[,counter]|@file} ][ --reconnect-timeout ][ --servercert sha1 ][ --useragent string ][ --os string ][https://]server[:port][/group]DESCRIPTION
The programopenconnectconnects to Cisco 'AnyConnect' VPN servers, which use standard TLSand DTLS protocols for data transport.The connection happens in two phases. First there is a simple HTTPSconnection over which the user authenticates somehow - by using acertificate, or password or SecurID, etc. Having authenticated, theuser is rewarded with an HTTP cookie which can be used to make thereal VPN connection.
The second phase uses that cookie in an HTTPSCONNECTrequest, and data packets can be passed over the resultingconnection. In auxiliary headers exchanged with theCONNECTrequest, a Session-ID and Master Secret for a DTLS connection are alsoexchanged, which allows data transport over UDP to occur.
OPTIONS
Any option except theconfigoption may be specified in the file.
By default, only stateless compression algorithms which do not maintain statefrom one packet to the next (and which can be used on UDP transports) areenabled. By setting the mode toallstateful algorithms (currently only zlib deflate) can be enabled. Or allcompression can be disabled by setting the mode tonone.
--force-dpd=INTERVALUseINTERVALas minimum Dead Peer Detection interval for CSTP and DTLS, forcing use of DPD even when the server doesn't request it.
Install Cisco Anyconnect Linux
On Windows, a relative directory for the default script will be handled asstarting from the directory that the openconnect executable is running from,rather than the current directory. The script will be invoked with thecommand-based script host cscript.exe.
Linux Cisco Anyconnect Vpn

PFS is available in Cisco ASA releases 9.1(2) and higher; a suitable ciphersuite may need to be manually enabled by the administrator using thessl encryptionsetting.
However, Cisco's support team has failed to give any competentresponse to the bug report and we don't know under what othercircumstances their bug might manifest itself. So this option existsto disable ALL re-use of HTTP sessions and cause a new connection to bemade for each request. If your server seems not to be recognising yourcertificate, try this option. If it makes a difference, please reportthis information to theopenconnect-devel [at] lists.infradead.orgmailing list.
This option is a temporary safety net, to work around potentialcompatibility issues with the code which falls back to the old methodautomatically. It causes OpenConnect to behave more like olderversions (4.08 and below) did. If you find that you need to use thisoption, then you have found a bug in OpenConnect. Please seehttp://www.infradead.org/openconnect/mail.html and report this to thedevelopers.
RSA SecurID secrets can be specified as an Android/iPhone URI or a raw numericCTF string (with or without dashes).
For Yubikey OATH the token secret specifies the name of the credential to beused. If not provided, the first OATH credential found on the device will beused.
FILENAME,if specified, can contain any of the above strings. Or, it can contain aSecurID XML (SDTID) seed.
If this option is omitted, and --token-mode is'rsa', libstoken will try to use the software token seed saved in~/.stokenrcby the 'stoken import' command.
SIGNALS
In the data phase of the connection, the following signals are handled:Cisco Anyconnect For Linux Ubuntu
